Improvements to Secrets Usage Monitoring in Zero
Zero has recently added two new features to help you detect unauthorized access to your secrets. In this post, I'll explain the new features and how they improve security.

Sam Magura

In a previous post, I talked about Secrets Usage History: What it is and why you should care. To summarize, it's important to monitor who accesses your API keys and other credentials so you can detect if one of these secrets falls into the wrong hands. Unauthorized access to your secrets can result in dire consequences, so a proactive approach is best here.
While everything in the original blog post is still accurate, I wanted to update you all on two recent enhancements in Zero that will enable you to track secrets usage history more effectively.
Secure your secrets conveniently
Zero is a modern secrets manager built with usability at its core. Reliable and secure, it saves time and effort.

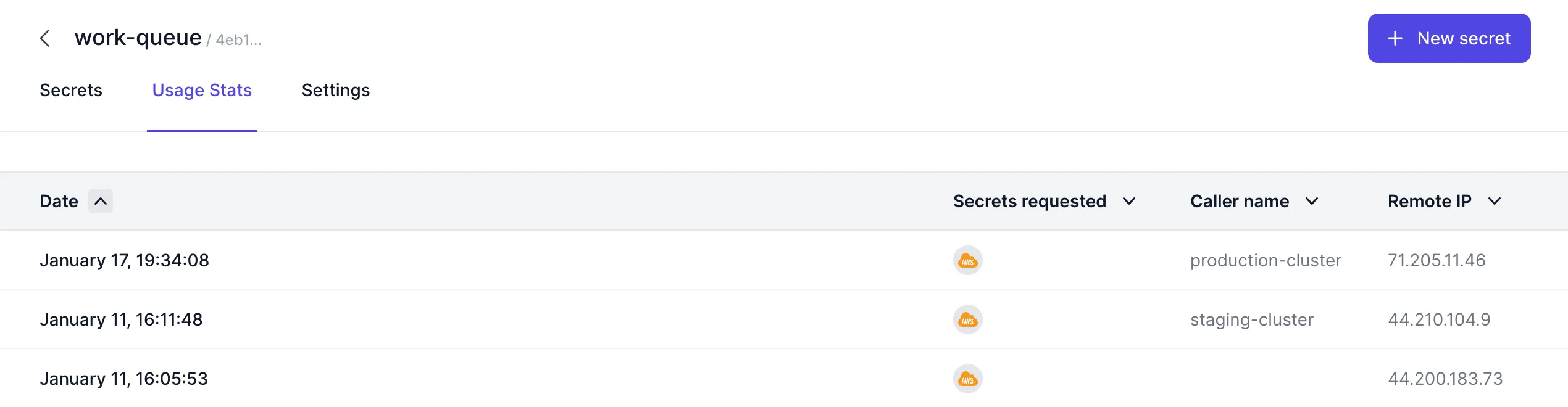
Caller Name
All of the Zero SDKs, as well as the Zero GraphQL API, now accept a callerName parameter which allows you to identify the machine the made the request to Zero. There are no restrictions on what string you can pass for the callerName, though you should ideally keep the callerName unique so that you can identify exactly where the request came from.
One strategy for setting the callerName is to use an environment variable that is different between your development, staging, and production environments. In TypeScript, this would look something like
If your Zero token is compromised, an attacker could use it to retrieve your secrets. But the attacker is likely to leave the caller name blank, or provide a bogus caller name that is easily distinguishable from your legitimate caller names. Therefore, if you always pass the callerName when retrieving secrets from Zero, you can easily identify unauthorized requests simply by reviewing the caller name column in the usage history table.
Global Usage History Dashboard
Previously, you could only view secrets usage history on a per-project basis. This made it inconvenient if you were trying to detect anomalous requests across all of your organization's projects.
Now, Zero has a global usage history table which shows requests for all projects. You'll see this table on the Dashboard, right after you log into Zero.
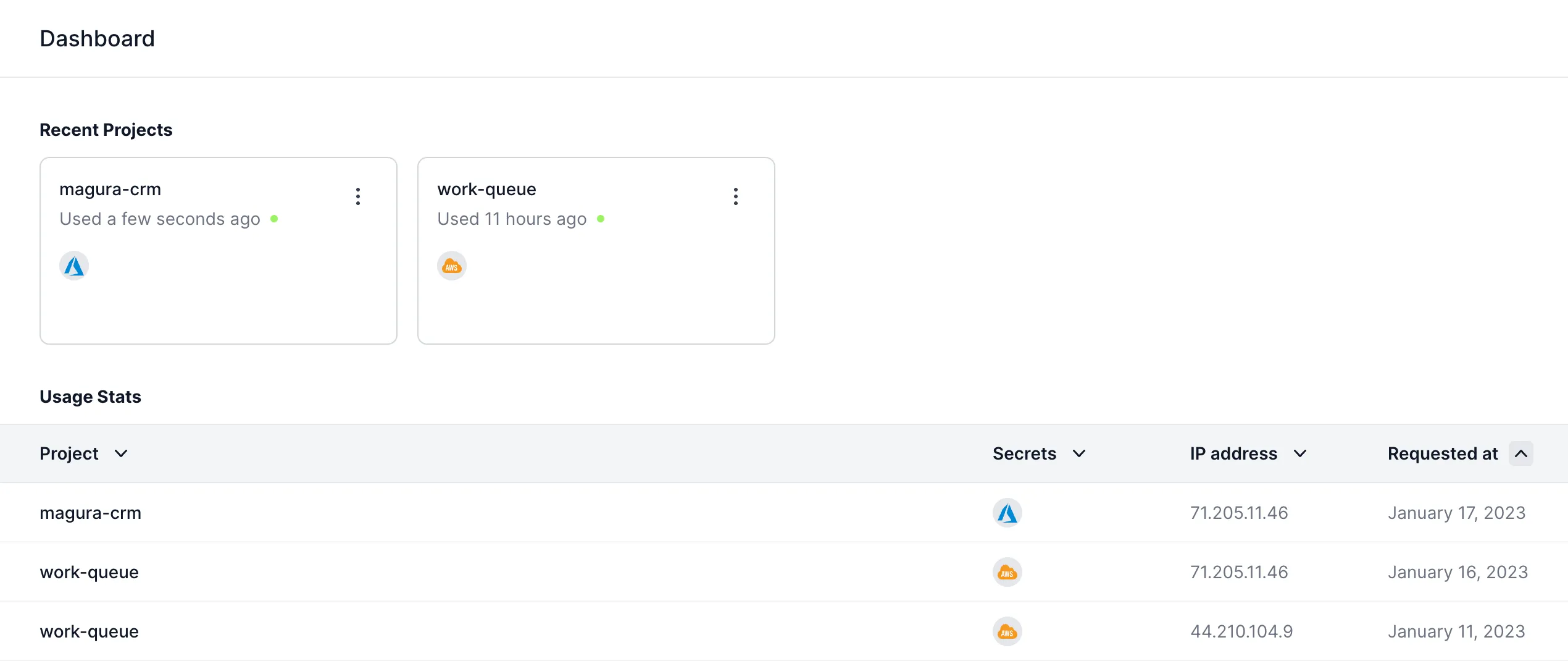
I really like that the global usage history table is front and center in the Zero UI, since this makes it hard not to review the request history for your secrets!
Looking Forward
The Zero team is committed to equipping you with best-in-class tools for protecting your secrets. In particular, the team is working on a feature that will automatically detect unusual access to your secrets — this should strengthen security for all users, even those who do not follow the best practice of regularly reviewing the usage history tables.
Other articles

Secrets Usage History: What it is and why it matters
If a secret is obtained by a malicious actor, the consequences can be severe. Monitoring the usage history of a secret in Zero allows you to detect unauthorized access and act before the secret is used in an exploit.

Announcing the Vercel Integration
The upcoming Zero Vercel integration will enable you to seamlessly sync secrets between Zero and the environment variables of your web apps hosted on Vercel!
Secure your secrets
Zero is a modern secrets manager built with usability at its core. Reliable and secure, it saves time and effort.